Built for modern enterprises
Seamlessly blending robust data security with intuitive user and file management for the modern business landscape
Spark Enterprise Accelerator
Unlock the transformative power of AI for your enterprise with the Spark Enterprise Accelerator Program. A dedicated journey tailored for businesses at every stage of AI adoption.
- Tailored AI Programs: From beginner to advanced, we have the perfect fit.
- Expert Guidance: Our AI professionals are with you at every step.
- Real-World Implementation: Experience hands-on AI application.
- Maximize ROI: Assess and capitalize on your AI investments.
Enterprise-Grade Security: Your Data, Your Control
The data and files you input into Spark are your sole property. They are not used for training AI models, are inaccessible to our team, and are never shared with other customers.
- File Uploads: Upload securely with top-tier encryption.
- Data Encryption: AES 256-bit at rest, TLS 1.2+ in transit.
- Certifications: ISO 27001 and SOC 2 certified.

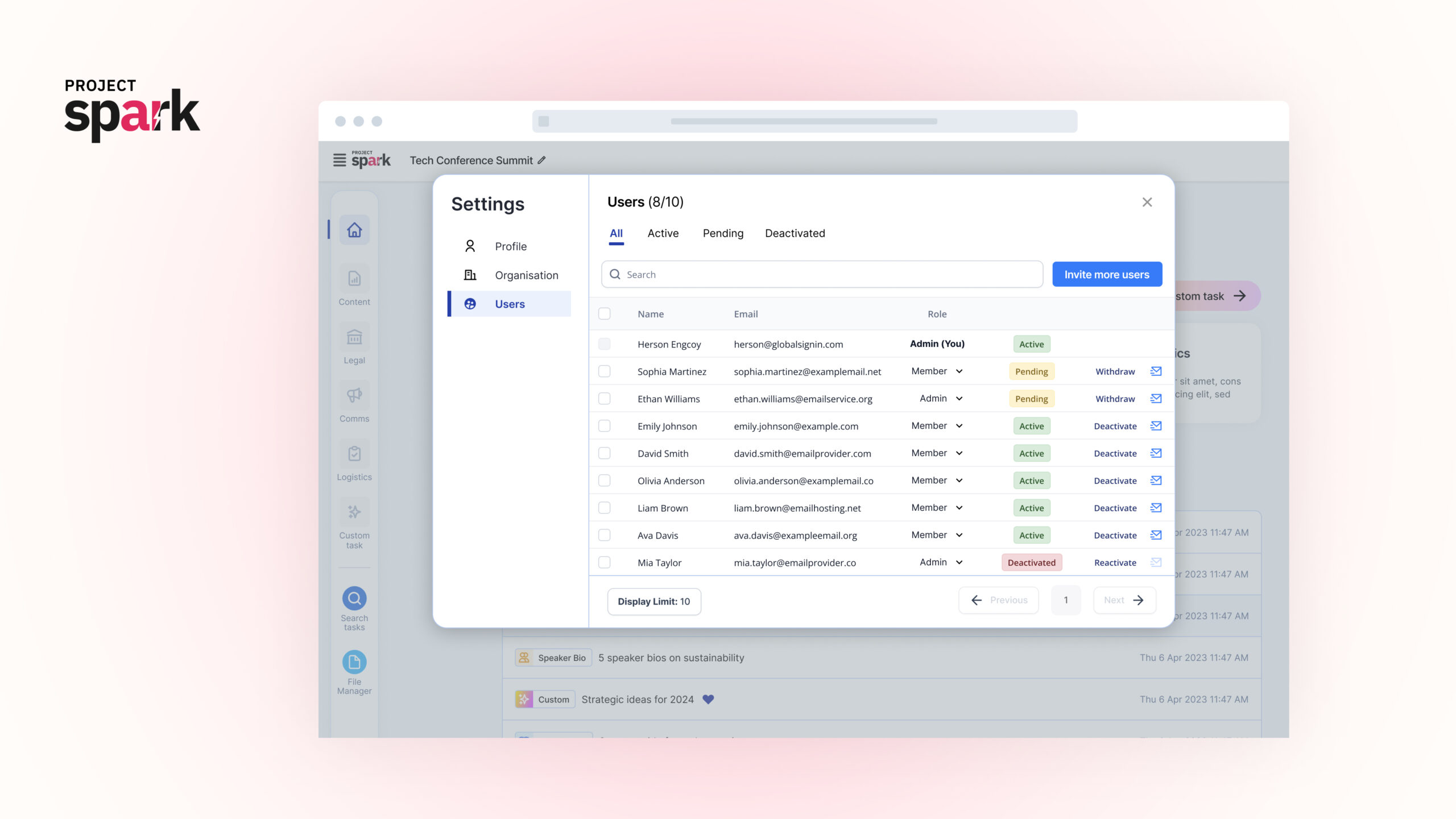
User & File Management
Spark Enterprise simplifies user and file management for modern businesses. Easily coordinate teams, handle files with confidence, and ensure the right people have the right access, all in one integrated platform.
- Upload and Manage Your Files Securely
- Manage your Organization's Users
- Control Who has Access to What